The Federal Emergency Management Agency (FEMA) plays a crucial role in helping communities prepare for and respond to natural disasters, emergencies, and potential terrorist attacks.
One of the critical aspects of FEMA’s work is conducting risk assessments to identify, analyze, and prioritize threats.
The FEMA risk assessment process is a structured approach that helps identify potential hazards, assess their impact, and provide guidance for effective countermeasures.
The first step in the FEMA risk assessment process is the identification and quantification of threats. This includes defining the threat and determining its likelihood by analyzing available information about potential aggressors and their history of hostile actions.
The outcome of this assessment results in the definition of the design basic threat, outlining the types and capabilities of weapons the building or infrastructure must be protected against.
Additionally, a threat rating is assigned, taking into account the probability of the threat occurring and the potential consequences of its occurrence.
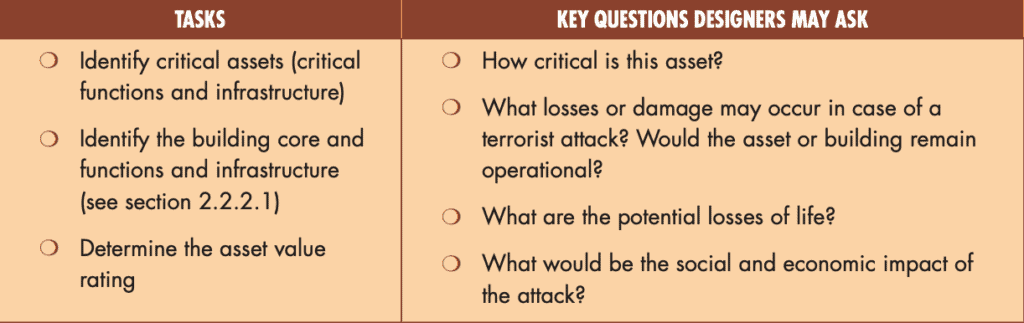
Once the threat is identified, the next step focuses on recognizing the assets that require protection. Assets include the building, people, equipment, and contents, as well as the potential consequences of damage or loss.
These assets are categorized based on the impact their incapacity or destruction would have on the overall operation of the facility or community.
Critical assets are identified, which encompass the core functions and processes necessary for the building to continue operating and providing services following an attack.
This step is essential for understanding the potential vulnerabilities of the infrastructure and determining appropriate countermeasures in the event of a threat.
Identifying and Defining Threats
In the FEMA Risk Assessment Process, the first step is to identify, define, and quantify potential threats.
In the context of terrorism, a threat can be any indication, circumstance, or event that has the potential to cause damage or loss to an asset, such as a building, people, equipment, and contents.
Collection of Threat Information
The process starts with collecting information about the aggressors (individuals or groups) known for their hostile actions, tactics, and types of weapons used.
Identifying the intentions of these groups and any potential targets is crucial in assessing the risk of terrorist attacks in specific areas or buildings.
Determining Design Basic Threat
Once the threats and their capabilities have been identified, it is time to determine the Design Basic Threat.
This defines the required level of protection for a building by specifying the types and capabilities of weapons against which it must be safeguarded.
The threat rating is based on the probability of a threat occurring and its consequences.
Threat Rating
The threat rating, on a scale of 1 to 10, is the result of assessing the likelihood and impact of a potential terrorist attack.
This numerical rating helps in prioritizing the mitigation measures needed to protect the assets. The higher the rating, the more urgent the need for protection.
To ensure a comprehensive risk assessment, designers should ask key questions such as: What groups or organizations are known?
Do they have a history of terrorist acts and what are their tactics? What are the intentions of these groups, and what type of targets do they choose?
Answering these questions will guide the development of effective countermeasures to minimize potential damage and loss.
By following these sub-sections in the FEMA Risk Assessment Process, the foundation for a thorough analysis of possible terrorist threats can be ensured.
This allows for informed decision-making and adequate preparation to minimize the impact of any potential attacks.
Asset Identification and Evaluation
Asset Categories
The first step in identifying and evaluating assets is to determine the categories they fall into. These typically include the building, people, equipment, and contents, as well as the consequences of their damage or loss.
The purpose of this categorization is to help prioritize assets based on the degree of debilitation impact caused by their incapacitation or destruction.
Core Functions Development
Identifying the core functions and processes necessary for a building to continue to operate and provide services after an attack is crucial.
This helps in the assessment and prioritization of critical assets, ensuring that essential operations can be restored as quickly as possible.
It is important to account for how these core functions are interdependent and the potential cascading effects of their disruption.
Furthermore, understanding the vulnerabilities of each core function can help in designing effective risk mitigation strategies.
Critical Asset Infrastructure
Critical asset infrastructure refers to the necessary systems and utilities that support the building’s operation and the delivery of services.
This includes elements such as power, water, telecommunications, and access control systems. Thorough identification and evaluation of these critical infrastructures are essential for risk assessment and for determining which protective measures should be implemented.
By comprehensively understanding the dependencies and vulnerabilities of these infrastructures, designers can develop strategies to enhance their resilience against potential threats.
In conclusion, effective asset identification and evaluation involve categorizing assets, determining their core functions and vulnerabilities, and identifying the critical infrastructures supporting them.
This process is vital in forming the foundation of a robust and comprehensive risk assessment, ultimately contributing to a secure and resilient building design.
Vulnerability Assessment of Assets
The vulnerability assessment process aims to evaluate the weaknesses and susceptibilities of an organization’s assets.
This includes examining the potential exposure to threats and evaluating the possible damage that could occur.
Vulnerability assessment plays a vital role in understanding how to mitigate risks and protect valuable assets. This section will focus on Asset Exposure and Potential Damage Evaluation.
Asset Exposure
Asset exposure is a critical component of the vulnerability assessment process. In this phase, it is essential to identify all the assets that could be at risk and categorize them based on their importance to the organization.
These assets can be physical, such as buildings and equipment, as well as intangible, such as the organization’s reputation and intellectual property.
During the asset exposure phase, some factors to consider include:
- The location of assets
- Accessibility and security measures in place
- Dependencies on other assets or external infrastructure
- The value of each asset to the organization
By understanding the exposure level of each asset, organizations can efficiently allocate resources and prioritize efforts to minimize vulnerabilities.
Potential Damage Evaluation
After identifying and categorizing assets, the next step in the vulnerability assessment process is to evaluate the potential damage that could occur due to various threats.
This involves analyzing the possible impacts on the organization’s operations, finances, reputation, and overall stability.
Some factors that may influence potential damage include:
- The severity and likelihood of various threats
- The effectiveness of existing security measures in mitigating threats
- The potential for cascading or compounding effects from a single incident
- The recovery time and resources required to restore normal operations
This evaluation helps organizations in developing targeted and effective mitigation strategies to protect their assets, reduce risks, and enhance overall security.
In conclusion, conducting a comprehensive vulnerability assessment of assets is crucial for any organization to understand its weaknesses and susceptibilities.
By examining asset exposure and potential damage evaluation, organizations can effectively allocate resources, prioritize efforts, and develop efficient mitigation strategies to protect valuable assets and reduce risks.
Probability and Severity Analysis
Measuring Probability
The first step in FEMA’s risk assessment process involves identifying, defining, and quantifying the threat. This is crucial in determining the likelihood of a potential terrorist attack against a particular asset.
To establish a threat rating, designers may inquire about the groups or organizations known to have a history of terrorist acts, their tactics, and their intentions, as outlined in the FEMA risk assessment process.
The threat rating is expressed on a scale of 1-10, which reflects the probability of the threat occurring and the consequences of its occurrence. This numerical value helps in further assessing the risks and guiding the necessary protective measures.
Assessing Severity
Once the probability has been determined, the next step is identifying the assets that need protection. Assets include buildings, people, equipment, contents, and the consequences of their damage or loss.
These assets can be categorized by the degree of debilitation impact that would be caused by their incapacity or destruction.
Critical assets comprise core functions and processes necessary for a building to continue operating and providing services after an attack, including infrastructure and utilities.
Understanding the severity of impact is essential in determining the extent of protection needed for these assets.
To thoroughly assess the severity, it’s essential to consider the types and capabilities of weapons that might be used in potential attacks as per FEMA’s guidance.
The outcome of this analysis is the design basic threat, which informs the protective measures against which a building must be guarded.
By combining the probability and severity of potential threats, designers can accurately determine the risks associated with each asset and implement appropriate mitigation options.
This thorough analysis ensures that both the building and its occupants will be as prepared and protected as possible in the event of a terrorist attack.
Implementing FEMA Guidelines
FEMA Risk Assessment Recommendations
The FEMA Risk Assessment Process involves a series of five steps that require a numerical importance rating on a scale of 1-10.
The first step involves identifying, defining, and quantifying the threat related to terrorism or any event that could lead to loss or damage to an asset.
Designers must gather information on potential aggressors and their tactics, leading to the determination of a design basic threat and threat rating.

In step two, the assets that need protection are identified, focusing on the building, people, equipment, and contents.
Assets are categorized based on the degree of debilitation impact that would be caused by their incapacity or destruction.
Critical assets include core functions and processes necessary for the building’s continued operation.
FEMA Guided Strategy Development
After identifying assets, the risk assessment process moves forward based on FEMA guidelines. This includes evaluating vulnerabilities and conducting a risk assessment considering threats and potential consequences.
Designers can use the information to develop security measures, which are then evaluated for their effectiveness and cost-efficiency.
Ultimately, the goal of implementing FEMA guidelines is to create a well-rounded security strategy that protects the most critical assets while still considering the constraints of budget and operational requirements.
By following the FEMA Risk Assessment Process and adhering to their recommendations, organizations can make informed decisions and design more secure environments.
Frequently Asked Questions
What are the five steps in the FEMA risk assessment process?
The FEMA risk assessment process consists of five consecutive steps:
- Identifying, defining, and quantifying the threat
- Identifying the assets (consequences) that need to be protected
- Assessing vulnerabilities
- Calculating risk
- Considering mitigation options
Each step results in a numerical value that expresses its importance, ranging from 1 to 10.
How is the threat level determined in the FEMA assessment?
The threat level in the FEMA assessment is determined by considering identified aggressors, their capabilities, and their history of hostile actions.
This includes the tactics and types of weapons that these threat actors have used in the past.
The outcome of the assessment is known as the design basic threat, which outlines the types and capabilities of weapons that the building needs protection against.
What factors are considered when identifying critical assets?
Critical assets refer to the building, people, equipment, and contents that could suffer significant damage or loss following an attack.
Factors considered when identifying critical assets include core functions, processes necessary for the building to operate after an attack, and the availability of infrastructure and utilities.
How does vulnerability assessment evaluate potential weaknesses?
Vulnerability assessment evaluates potential weaknesses in the building and its assets by considering factors such as physical security, structural integrity, and accessibility.
This process examines how well the identified assets are protected from threats and identifies any areas in need of improvement.
What method is used to calculate risk in FEMA’s process?
FEMA’s risk assessment process calculates risk by assigning numerical importance ratings from 1 to 10 for each step, from threat identification to vulnerability assessment.
The overall risk assessment is derived by considering these ratings along with the predicted consequences of an attack and the likelihood of its occurrence.
How are mitigation options selected based on the risk assessment results?
Mitigation options are chosen based on the risk assessment results by weighing the effectiveness of each proposed countermeasure against the identified risks.
Decision-makers will prioritize options that are most likely to reduce or eliminate the threat, with consideration given to the cost, feasibility, and potential side effects of each intervention.